43 security labels are used in what type of model
Types of Intelligence Collection - Intelligence Studies - LibGuides at ... Communications Intelligence (COMINT) is a type of SIGINT and refers to the interception of communications between two parties. U.S. SIGINT satellites are designed and built by the National Reconnaissance Office, although conducting U.S. signals intelligence activities is primarily the responsibility of the National Security Agency (NSA). xgboost/sklearn.py at master · dmlc/xgboost · GitHub Metric used for monitoring the training result and early stopping. It can be a. string or list of strings as names of predefined metric in XGBoost (See. doc/parameter.rst), one of the metrics in :py:mod:`sklearn.metrics`, or any other. user defined metric that looks like `sklearn.metrics`.
GUI Testing Tutorial: User Interface (UI) TestCases with Examples - Guru99 Demo: How to do GUI Test. Here we will use some sample test cases for the following screen. Following below is the example of the Test cases, which consists of UI and Usability test scenarios. TC 01- Verify that the text box with the label " Source Folder " is aligned properly.
Security labels are used in what type of model
The Registration Process With Spring Security - Baeldung When the controller receives the request "/user/registration", it creates the new UserDto object that will back the registration form, binds it, and returns - pretty straightforward. 5. Validating Registration Data. Next - let's look at the validations that the controller will perform when registering a new account: FISMA Assessment and Authorization (A&A) Guidance - NCI Security and ... A&A Introduction. Welcome to the NCI Information System Assessment and Authorization (A&A) information and guidance page. The information provided here is intended to supplement guidance provided by the National Institute of Standards and Technology (NIST) and NIH to provide best practices for managing the A&A process (A&A was formerly called security assessment and authorization (SA&A) and ... Radiation and Airport Security Scanning | US EPA Airport security systems use metal detectors, backscatter x-ray machines, millimeter wave scanners, and cabinet x-ray machines to keep people safe while traveling; Some security devices use ionizing radiation to scan luggage. Safety measures are in place to make sure it does not expose workers and travelers to high-levels of ionizing radiation.
Security labels are used in what type of model. Choose Microsoft Purview Information Protection built-in labeling for ... In this article. Microsoft 365 licensing guidance for security & compliance.. When you use sensitivity labels in Microsoft 365 Apps on Windows computers, you have a choice of using labeling that's built into Office apps, or an add-in from the Azure Information Protection (AIP) unified labeling client.. Built-in labeling forms the cornerstone of a Microsoft Purview information protection ... Create a Power BI datamart in minutes Row Level Security (RLS) for datamart Open your datamart and find the RLS role creation and management option in the Ribbon. Click manage role to create roles and assign them. Finally, you can use the 'View as' option to see the data access for the created roles. It's that simple. Row Level Security Sensitivity Label Issues · iree-org/iree · GitHub 3. [vulkan] Float remainder numeric issue on various GPUs bug codegen/spirv. #9670 opened 16 days ago by antiagainst. 2. Failure to lower mhlo.scatter to LinalgExt bug integrations/mhlo. #9669 opened 17 days ago by dan-garvey IREE + NOD Model Coverage. Device security | Cloud IoT Core Documentation | Google Cloud Security standards Cloud IoT Core uses digital signature-based authentication, for both RSA and Elliptic Curve signed tokens. The following specific algorithms are supported: JWT RS256...
Continuous evaluation overview | AI Platform Prediction - Google Cloud Ground truth labels are what humans determine to be the correct labels for your machine learning task. Continuous evaluation uses these as an answer key and calculates metrics by comparing your model version's predictions to the ground truth labels. When you create an evaluation job, you must decide how you want to generate ground truth labels ... All 8 Models of Communication, Explained! - Helpful Professor This model was the first to introduce the role of noise in the communication process. The idea of feedback was retroactively introduced to this model. 4. Berlo's S-M-C-R Model One Sentence Overview: Berlo's S-M-C-R model explains communication in four steps: Source, Message, Channel, and Receiver. Managing models with Vertex AI | BigQuery ML | Google Cloud To delete the model, you must first undeploy the model from Vertex AI Model Registry, return to BigQuery ML, and then delete it. DROP MODEL [PROJECT_ID].[DATASET_ID].[BQML_MODEL_ID] Important: For now models registered to Vertex AI can only be deleted via DROP MODEL SQL command. The other deleting model, e.g. from API / JAVA / Python client is ... How To Build A Security-First Cloud Framework That Puts You In Control Once your CIO and CISO are in sync, here are three more crucial steps in building a cloud-native security model. Step 1: Know your risks and define a clear security strategy PwC's Cloud Business...
Collateral - Definition, Collateral Value, Security & Liens Collateral is an asset pledged by a borrower, to a lender (or a creditor), as security for a loan. Borrowers generally seek credit in order to purchase things - it could be a house or a car for an individual, or it could be manufacturing equipment, commercial real estate, or even something intangible (like intellectual property) for a business. Get started with sensitivity labels - Microsoft Purview (compliance) When you're ready to start protecting your organization's data by using sensitivity labels: Create the labels. Create and name your sensitivity labels according to your organization's classification taxonomy for different sensitivity levels of content. Use common names or terms that make sense to your users. How To Classify Data In Python using Scikit-learn - ActiveState For more information about labeled data, refer to: How to label data for machine learning in Python. Types of Classification. There are two main types of classification: Binary Classification - sorts data on the basis of discrete or non-continuous values (usually two values). For example, a medical test may sort patients into those that have ... Apply encryption using sensitivity labels - Microsoft Purview ... Finally, as an admin, when you configure a sensitivity label to apply encryption, you can choose either to: Assign permissions now, so that you determine exactly which users get which permissions to content with that label. Let users assign permissions when they apply the label to content. This way, you can allow people in your organization ...
What is the CIA Triad? - Varonis Combining security models and frameworks The CIA triad is a helpful model for organizations with pressing data needs and requirements. Used in conjunction with other frameworks, it can serve as a guiding model to more effective and balanced processes, tools, and policies. To find out how to better protect your data, check out Varonis DatAdvantage.
SimpliSafe Home Security System Review 2022 | U.S. News SimpliSafe offers a DIY home security system that's budget-priced but still has an array of features. Professional monitoring plans cost $17.99 a month and up and are controlled by a keypad with ...
Power BI security white paper - Power BI | Microsoft Docs The decades-old foundations of the BI security model - object-level and row-level security - while still important, clearly no longer suffice for providing the kind of security needed in the cloud era. Instead, organizations must look for a cloud-native, multi-tiered, defense-in-depth security solution for their business intelligence data.
Types of alerting policies | Cloud Monitoring | Google Cloud Alerting policies define conditions that watch for three things: Some metric behaving in some way for some period of time. For example, an alerting policy might trigger when the value of a metric goes higher than a threshold, or when the value changes too quickly. This content does not apply to log-based alerting policies.
Introduction To Classic Security Models - GeeksforGeeks There are 3 main types of Classic Security Models. Bell-LaPadula Biba Clarke Wilson Security Model 1. Bell-LaPadula This Model was invented by Scientists David Elliot Bell and Leonard .J. LaPadula .Thus this model is called the Bell-LaPadula Model. This is used to maintain the Confidentiality of Security.
Domain Name System (DNS) in Application Layer - GeeksforGeeks DNS is a hostname for IP address translation service. DNS is a distributed database implemented in a hierarchy of name servers. It is an application layer protocol for message exchange between clients and servers. Requirement: Every host is identified by the IP address but remembering numbers is very difficult for the people also the IP ...
AlumiGuard® Metal Asset Tags - Aluminum Asset Tags All asset tags are available in a variety of text colors. You will be able to choose tag color on next page. Step 1: Select a Size Select a size for your label. You will be able to select a design, change color, personalize text and specify your numbering on the next page. Best Seller 0.75" x 1.5" Best Seller 0.75" x 2" 1" x 2" 0.5" x 1.25"
Learn about sensitivity labels - Microsoft Purview (compliance) In all these cases, sensitivity labels from Microsoft Purview can help you take the right actions on the right content. With sensitivity labels, you can classify data across your organization, and enforce protection settings based on that classification. That protection then stays with the content. For more information about these and other ...
Identity-Aware Proxy overview | Google Cloud This page describes the basic concepts of Identity-Aware Proxy (IAP), a Google Cloud global service. IAP lets you establish a central authorization layer for applications accessed by HTTPS, so you can use an application-level access control model instead of relying on network-level firewalls. IAP policies scale across your organization.
25 Top Business Intelligence Tools (Best BI Tools in 2022) Supports interactive data visualization and instant access to company data. #30) Artus: Artus is a BI platform from Bitam. Artus monitors key performance metrics and comes with SaaS and On-premise deployment. The combination of management dashboards and ad-hoc analysis is the best feature of Artus.
Radiation and Airport Security Scanning | US EPA Airport security systems use metal detectors, backscatter x-ray machines, millimeter wave scanners, and cabinet x-ray machines to keep people safe while traveling; Some security devices use ionizing radiation to scan luggage. Safety measures are in place to make sure it does not expose workers and travelers to high-levels of ionizing radiation.
FISMA Assessment and Authorization (A&A) Guidance - NCI Security and ... A&A Introduction. Welcome to the NCI Information System Assessment and Authorization (A&A) information and guidance page. The information provided here is intended to supplement guidance provided by the National Institute of Standards and Technology (NIST) and NIH to provide best practices for managing the A&A process (A&A was formerly called security assessment and authorization (SA&A) and ...
The Registration Process With Spring Security - Baeldung When the controller receives the request "/user/registration", it creates the new UserDto object that will back the registration form, binds it, and returns - pretty straightforward. 5. Validating Registration Data. Next - let's look at the validations that the controller will perform when registering a new account:





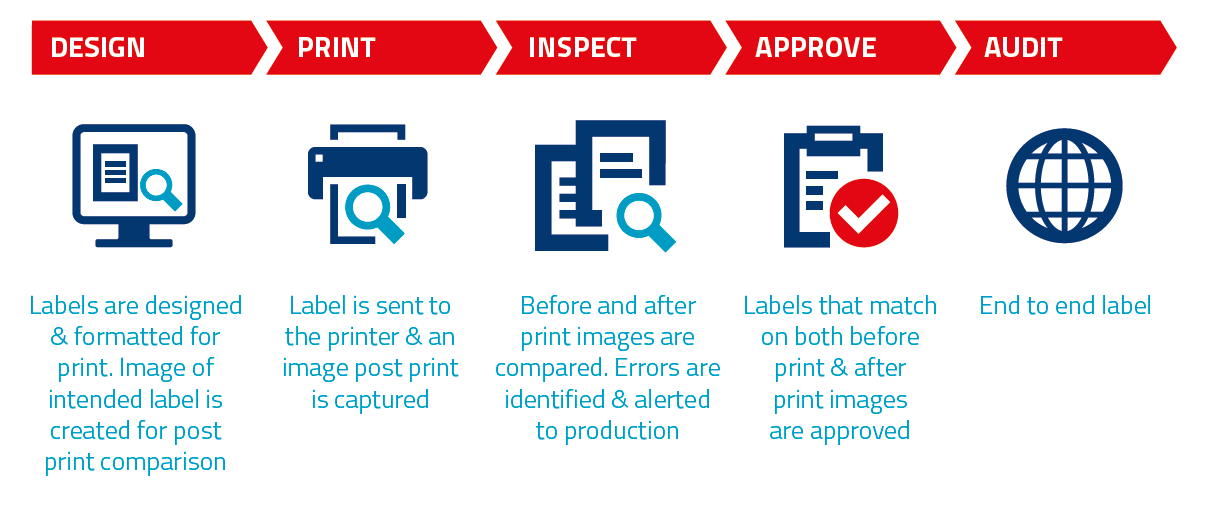










Post a Comment for "43 security labels are used in what type of model"